[MikroTik] ip route> /ip address print Flags: X - disabled, I - invalid, D - dynamic # ADDRESS NETWORK BROADCAST INTERFACE 0 10.0.0.217/24 10.0.0.217 10.0.0.255 Public 1 192.168.0.254/24 192.168.0.254 192.168.0.255 Local [MikroTik] ip route> add dst-address=192.168.1.0/24 gateway=192.168.0.50 [MikroTik] ip route> add gateway=10.0.0.1
There are several ways of viewing the routes:
[MikroTik] ip route> print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 S 192.168.1.0/24 r 192.168.0.50 1 Local
1 S 0.0.0.0/0 r 10.0.0.1 1 Public
2 DC 192.168.0.0/24 r 0.0.0.0 0 Local
3 DC 10.0.0.0/24 r 0.0.0.0 0 Public
[MikroTik] ip route> print detail
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
0 S dst-address=192.168.1.0/24 preferred-source=0.0.0.0
gateway=192.168.0.50 gateway-state=reachable distance=1
interface=Local
1 S dst-address=0.0.0.0/0 preferred-source=0.0.0.0 gateway=10.0.0.1
gateway-state=reachable distance=1 interface=Public
2 DC dst-address=192.168.0.0/24 preferred-source=192.168.0.254
gateway=0.0.0.0 gateway-state=reachable distance=0 interface=Local
3 DC dst-address=10.0.0.0/24 preferred-source=10.0.0.217 gateway=0.0.0.0
gateway-state=reachable distance=0 interface=Public
[MikroTik] ip route> print column="dst-address gateway interface "
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
# DST-ADDRESS GATEWAY INTERFACE
0 S 192.168.1.0/24 192.168.0.50 Local
1 S 0.0.0.0/0 10.0.0.1 Public
2 DC 192.168.0.0/24 0.0.0.0 Local
3 DC 10.0.0.0/24 0.0.0.0 Public
[MikroTik] ip route>
Description of the arguments:
number - number assigned to the item in the list
flag - shows the status of the item
type - type of the route shows "where it came from" (connected / static / RIP / OSPF)
dst-address/netmask - destination address and network mask, where mask is number of bits in the subnet mask.
gateway - gateway host, that can be reached directly through some of the interface. You can specify multiple gateways separated by period "," for equal cost multipath routes. See more information on that below.
gateway-state - shows the status of the next hop. Can be "r" (reachable).
preferred-source - source address of packets leaving the router via this route. Must be a valid address of the router, which is assigned to the router's interface, where the packet leaves. Default value is 0.0.0.0, i.e., it is determined at the time of sending the packet out through the interface.
interface - interface through which the gateway can be reached. If (unknown), then the gateway cannot be reached directly, or the route has been disabled.
distance - administrative distance of the route. When forwarding a packet the router will use the route with the lowest administrative distance and reachable gateway.
Equal Cost Multipath Routing
Equal cost multipath routing feature can be used for load balancing.
It is implemented in the MikroTik RouterOS according to the RFC2328.
New gateway is chosen for new source/destination IP pair. This means that, for example, one FTP connection will use only one link, but new connection to different server will use other link. So on big backbones this should distribute traffic fine. Also this has another good feature - single connection packets do not get reordered and therefore do not kill TCP performance.
Equal cost multipath routes can be created by routing protocols (RIP or OSPF), or adding a static route with multiple gateways. The routing protocols may create routes with equal cost automatically, if the cost of the interfaces is adjusted properly. For more information on using the routing protocols, please read the corresponding section of the Manual.
To create a static multipath route, specify the gateway argument in the form "gateway=x.x.x.x,y.y.y.y", for example:
[MikroTik] ip route> print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 S 192.168.1.0/24 r 192.168.0.50 1 Local
1 S 0.0.0.0/0 r 10.0.0.1 1 Public
2 DC 192.168.0.0/24 r 0.0.0.0 0 Local
3 DC 10.0.0.0/24 r 0.0.0.0 0 Public
[MikroTik] ip route> set 0 gateway=192.168.0.50,192.168.0.51,10.0.0.17
[MikroTik] ip route> print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 S 192.168.1.0/24 r 192.168.0.50 1 Local
r 192.168.0.51 Local
r 10.0.0.17 Public
1 S 0.0.0.0/0 r 10.0.0.1 1 Public
2 DC 192.168.0.0/24 r 0.0.0.0 0 Local
3 DC 10.0.0.0/24 r 0.0.0.0 0 Public
[MikroTik] ip route>
Policy Routing
Policy Routing is a new feature in the V2.4 of MikroTik RouterOS.
Policy routing is implemented using multiple routing tables and list of
rules that specify how these tables should be used.
The Policy Routing is implemented in the MikroTik RouterOS based on source and destination addresses of the packet and on the interface the packet arrives at the router.
Note! Policy routing will not function 'as desired' for packets originated from the router or masqueraded packets. It is because these packets have source address 0.0.0.0 at the moment when they are processed by the routing table. Therefore it is not possible to have masquerading with different source addresses.
When finding the route for a packet, the packet is matched against policy routing rules one after another, until some rule matches the packet. Then action specified in that rule is executed. If no rule matches the packet, it is assumed that there is no route to given host and appropriate action is taken (packet dropped and ICMP error sent back to the source).
If the routing table does not have a route for the packet, next rule after the one that directed to current table is examined, until either route is found, end of rule list is reached, or some rule with action drop or unreachable is hit.
This way it is good to have last rule say "from everywhere to everywhere, all interfaces, lookup main route table", because then gateways can be found (connected routes are entered in the main table only).
Action for the rule can be one of:
Policy routing rules are configured in /ip policy-routing rule menu
[MikroTik] ip policy-routing rule> print Flags: X - disabled, I - invalid # SRC-ADDRESS DST-ADDRESS INTE... FLOW ACTION TABLE 0 0.0.0.0/0 0.0.0.0/0 all lookup main [MikroTik] ip policy-routing rule>
After installation, there is one default rule, which says that routes for all packets should be looked up in the "main" table. Argument description:
src-address/mask - Source IP address/mask, where mask is number of bits in the subnet. For example, x.x.x.x/32 for the address x.x.x.x and the 32-bit netmask 255.255.255.255
dst-address/mask - Destination IP address/mask, where mask is number of bits in the subnet.
interface - Interface name through which the packet arrives. Should be 'all' for the rule that should match locally generated or masqueraded packets, since at the moment of processing the routing table these packets have interface name set to loopback.
flow - flow mask of the packet to be matched by this rule. The flow masks are set using '/ip firewall mangle'.
Routing tables can be created/deleted in the '/ip policy-routing' menu:
[MikroTik] ip policy-routing> print Flags: D - dynamic # NAME 0 D main [MikroTik] ip policy-routing>
There is always the table "main" - this one can not be deleted and its name can not be changed. The "main" table is routing table that can be changed by issuing commands in the '/ip route' menu.
A new table can be added:
[MikroTik] ip policy-routing> add name=karlis [MikroTik] ip policy-routing> print Flags: D - dynamic # NAME 0 karlis 1 D main [MikroTik] ip policy-routing>
Routes in a routing table can be added/removed/changed in '/ip policy-routing table _table-name_' menu:
[MikroTik] ip policy-routing> table karlis [MikroTik] ip policy-routing table karlis> add dst-address=10.5.5.0/24 gateway=10.0.0.22 [MikroTik] ip policy-routing table karlis> print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS G GATEWAY DISTANCE INTERFACE 0 static 10.5.5.0/24 r 10.0.0.22 1 Public [MikroTik] ip policy-routing table karlis>
The "main" table is the same as one in '/ip route':
[MikroTik] ip policy-routing> table main
[MikroTik] ip policy-routing table main> print
Flags: X - disabled, I - invalid, D - dynamic, R - rejected
# TYPE DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 static 192.168.1.0/24 r 192.168.0.50 1 Local
1 static 0.0.0.0/0 r 10.0.0.1 1 Public
2 D connect 192.168.0.0/24 r 0.0.0.0 0 Local
3 D connect 10.0.0.0/24 r 0.0.0.0 0 Public
[MikroTik] ip policy-routing table main>
[MikroTik] ip policy-routing table main> /ip route print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 S 192.168.1.0/24 r 192.168.0.50 1 Local
1 S 0.0.0.0/0 r 10.0.0.1 1 Public
2 DC 192.168.0.0/24 r 0.0.0.0 0 Local
3 DC 10.0.0.0/24 r 0.0.0.0 0 Public
[MikroTik] ip policy-routing table main>
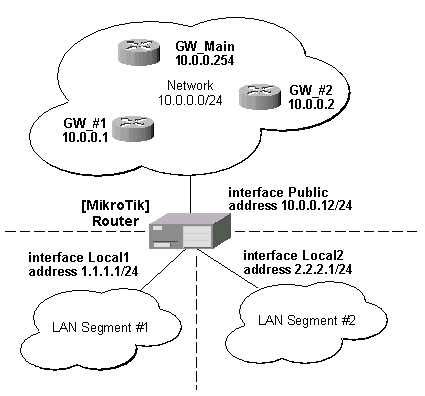
We want packets coming from 1.1.1.0/24 use gateway 10.0.0.1 and packets from 2.2.2.0/24 use gateway 10.0.0.2. And the rest of packets use gateway 10.0.0.254 (assuming we already have it so):

Commands to achieve this:
Add 2 new routing tables:
[MikroTik] ip policy-routing> add name=from_net1 add name=from_net2 [MikroTik] ip policy-routing> print Flags: X - disabled # NAME 0 from_net1 1 from_net2 2 main [MikroTik] ip policy-routing>
Create the default route in each of the tables:
[MikroTik] ip policy-routing> table from_net1 add gateway=10.0.0.1 table from_net2 add gateway=10.0.0.2 [MikroTik] ip policy-routing> table from_net1 print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS NEXTHOP-S... GATEWAY DISTANCE INTERFACE 0 static 0.0.0.0/0 A 10.0.0.1 1 Public [MikroTik] ip policy-routing> table from_net2 print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS NEXTHOP-S... GATEWAY DISTANCE INTERFACE 0 static 0.0.0.0/0 A 10.0.0.2 1 Public [MikroTik] ip policy-routing>
Create rules that will direct traffic from sources to given tables, and arrange them in the desired order:
[MikroTik] ip policy-routing> rule [MikroTik] ip policy-routing rule> print Flags: X - disabled, I - invalid # SRC-ADDRESS DST-ADDRESS INTERFACE ACTION TABLE 0 0.0.0.0/0 0.0.0.0/0 all lookup main [MikroTik] ip policy-routing rule> add src-address=1.1.1.1/32 action=lookup table=main add src-address=2.2.2.1/32 action=lookup table=main add src-address=1.1.1.0/24 action=lookup table=from_net1 add src-address=2.2.2.0/24 action=lookup table=from_net2 [MikroTik] ip policy-routing rule> print Flags: X - disabled, I - invalid # SRC-ADDRESS DST-ADDRESS INTERFACE ACTION TABLE 0 0.0.0.0/0 0.0.0.0/0 all lookup main 1 1.1.1.1/32 0.0.0.0/0 all lookup main 2 2.2.2.1/32 0.0.0.0/0 all lookup main 3 1.1.1.0/24 0.0.0.0/0 all lookup from_net1 4 2.2.2.0/24 0.0.0.0/0 all lookup from_net2 [MikroTik] ip policy-routing rule> move 0 4 [MikroTik] ip policy-routing rule> print Flags: X - disabled, I - invalid # SRC-ADDRESS DST-ADDRESS INTERFACE ACTION TABLE 0 1.1.1.1/32 0.0.0.0/0 all lookup main 1 2.2.2.1/32 0.0.0.0/0 all lookup main 2 1.1.1.0/24 0.0.0.0/0 all lookup from_net1 3 2.2.2.0/24 0.0.0.0/0 all lookup from_net2 4 0.0.0.0/0 0.0.0.0/0 all lookup main [MikroTik] ip policy-routing rule>
Here the rules #0 and #1 are needed to pocess correctly connections from the local networks to the local addresses of the router. Namely, the 'connected' routes from the main table should be used instead of using the default routes from table from_net1 or from_net2. Rules #2 and #3 will handle packets with destination other than locally connected networks.