Remark: To use a private address space, NAT is not required. It is required only to map one global IP address and/or port to a local one. Typically, masquerading (a firewall feature) is used to masquerade the local inside network addresses and ports to one global outside IP address and ports.
Please consult the Basic Setup Guide and the Firewall Manual for more information on masquerading.
The NAT rules are applied in the following order:
For more information about NAT, see RFC 1631. For example, you can visit this site: http://www.faqs.org/rfcs/rfc1631.html
[MikroTik] ip firewall static-nat>
NAT allows to translate addresses and ports of IP packets as they leave or
enter the router. This allows to use IP address space more efficiently.
add Add new NAT rule
comment Set rule comment
disable Disable rule
enable Enable rule
export Export rules
find Find NAT rules
get Get value of item's property
move Move rule
print Show NAT rules
remove Remove NAT rule
set Change NAT rule
[MikroTik] ip firewall static-nat>
NAT can be managed through the JAVA Console as well. Go to IP/Firewall and open the Static NAT window by pressing the button with two arrows.
Adding a NAT Rule
Usually there are two NAT rules required for mapping one address:port to another one.
One rule is required for mapping incoming packets, one for outgoing packets of a connection.
Only in cases of udp packets (one-directional packet flow), it is enough with
just one NAT rule to modify the packet's address and/or port.
NAT rules can be added using the /ip firewall static-nat add command. The argument description is as follows:
src-address - Source IP address. Can be in the form address/mask:ports, where mask is number of bits in the subnet, and ports is one port, or range of ports, e.g., x.x.x.x/32:80-81
src-netmask - Source netmask in decimal form x.x.x.x
src-port - Source port number or range (0-65535). 0 means all ports 1-65535.
dst-address - Destination IP address. Can be in the form address/mask:ports, where mask is number of bits in the subnet, and ports is one port, or range of ports, e.g., x.x.x.x/32:80-81
dst-netmask - Destination netmask in decimal form x.x.x.x
dst-port - Destination port number or range (0-65535). 0 means all ports 1-65535.
to-src-address - Translated source IP address. Can be in the form address/mask:ports, where mask is number of bits in the subnet, and ports is one port, or range of ports, e.g., x.x.x.x/32:80-81
to-src-netmask - Translated source netmask
to-src-port - Source port number. 0 means no change (leave as it was).
to-dst-address - Translated destination IP address. 0.0.0.0 means no change. Can be in the form address/mask:ports, where mask is number of bits in the subnet, and ports is one port, or range of ports, e.g., x.x.x.x/32:80-81
to-dst-netmask - Translated destination netmask
to-dst-port - Translated destination port number. 0 means no change (leave as it was).
interface - Interface, for which the rule should be used
protocol - Protocol
translate - translate or not (yes/no). If 'no', then the packet is passed through without translation, and no more NAT rules are processed.
direction - direction of the packet regarding the interface. 'in' means from the interface into the router, and 'out' means from the router to the interface.
The existing NAT rules can be listed using the /ip firewall static-nat print command. Example output is:
[MikroTik]> ip firewall static-nat
[MikroTik] ip firewall static-nat> print
Flags: X - disabled, I - invalid
0 interface=Public src-address=0.0.0.0/0:0-65535 dst-address=10.1.1.12/32:80
protocol=tcp to-src-address=0.0.0.0/0:0 to-dst-address=192.168.0.17/32:80
translate=yes direction=in
1 interface=Public src-address=192.168.0.17/32:80 dst-address=0.0.0.0/0:0-65535
protocol=tcp to-src-address=10.1.1.12/32:80 to-dst-address=0.0.0.0/0:0
translate=yes direction=out
[MikroTik] ip firewall static-nat>
For argument description see the add command above.
The NAT rule parameters can be changed using the /ip firewall static-nat set # command, where the # is the NAT rule number obtained from the print command.
NAT rules are processed in the order they appear under the /ip firewall static-nat print command list. Use the /ip firewall static-nat move #1 #2 command to change the order of NAT rules. Here, the #1 is current number of the rule in the list, whereas the #2 is the desired number of the rule.
NAT rules can be enabled or disabled using the /ip firewall static-nat enable # and /ip firewall static-nat disable # commands. Disabled NAT rules are not processed.
Further on, several examples of using NAT are given arranged according to complexity:
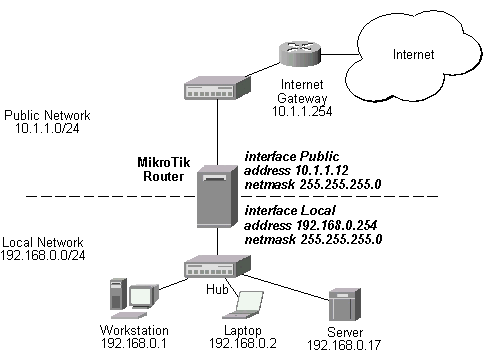
Assume we want to map external address 10.1.1.12 and port 8080 to the internal address 192.168.0.17 and port 80. The basic network setup is in the following diagram:

The IP addresses and routes of the MikroTik router are as follows:
[MikroTik] ip address> print Flags: X - disabled, I - invalid, D - dynamic # ADDRESS NETWORK BROADCAST INTERFACE 0 192.168.0.254/24 192.168.0.0 192.168.0.255 Local 1 10.1.1.12/24 10.1.1.0 10.1.1.255 Public [MikroTik] ip address> /ip route print Flags: X - disabled, I - invalid, D - dynamic, R - rejected # TYPE DST-ADDRESS NEXTHOP-S... GATEWAY DISTANCE INTERFACE 0 static 0.0.0.0/0 A 10.1.1.254 1 Public 1 D connect 192.168.0.0/24 A 0.0.0.0 0 Local 2 D connect 10.1.1.0/24 A 0.0.0.0 0 Public [MikroTik] ip address>
Two static NAT rules are required for translating the address:port - one for the incoming packets, and one for the outgoing packets:
[MikroTik]> ip firewall static-nat
[MikroTik] ip firewall static-nat>
add dst-address 10.1.1.12/32:8080 protocol tcp \
direction in interface Public translate yes \
to-dst-address 192.168.0.17/32:80
add src-address 192.168.0.17/32:80 protocol tcp \
direction out interface Public translate yes \
to-src-address 10.1.1.12/32:8080
[MikroTik] ip firewall static-nat> print
Flags: X - disabled, I - invalid
0 interface=Public src-address=0.0.0.0/0:0-65535 dst-address=10.1.1.12/32:8080
protocol=tcp to-src-address=0.0.0.0/0:0 to-dst-address=192.168.0.17/32:80
translate=yes direction=in
1 interface=Public src-address=192.168.0.17/32:80 dst-address=0.0.0.0/0:0-65535
protocol=tcp to-src-address=10.1.1.12/32:8080 to-dst-address=0.0.0.0/0:0
translate=yes direction=out
[MikroTik] ip firewall static-nat>
From the global network, the server can be accessed at 10.1.1.12:8080.
From the local network, the server can be accessed at 192.168.0.17:80.
The server cannot be accessed at 10.1.1.12:8080 from the local network.
It is due to the fact, that the server sees request coming from its own network,
and it responds back directly, i.e., bypassing the router and the NAT rule.
Please see the further examples for enabling the use of global address 10.1.1.12:8080
for accessing the server locally.
Example of NAT with Masquerading
Since we use masquerading for the Local network 192.168.0.0/24 (see the Application Example above),
we should exclude masquerading for the server's address 192.168.0.17
and TCP port 80 by adding a rule with action 'accept' to the forward chain.
The second rule would masquerade everything else:
[MikroTik]> ip firewall rule forward
[MikroTik] ip firewall rule forward >
add src-address 192.168.0.17/32:80 protocol tcp interface Public
add src-address 192.168.0.0/24 action masq interface Public
[MikroTik] ip firewall rule forward> print
Flags: X - disabled, I - invalid
0 protocol=tcp src-address=192.168.0.17/32:80
dst-address=0.0.0.0/0:0-65535 interface=Public action=accept
tcp-options=all log=no
1 protocol=all src-address=192.168.0.0/24:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=masq
tcp-options=all log=no
[MikroTik] ip firewall rule forward>
The ftp uses TCP port 21 on the server for establishing the connection, and the server's tcp port 20 when connecting back to the client for data connections.
To translate the addresses and ports, totally four static NAT rules would be required. However, ports 20 and 21 can be grouped in a port range, and only two rules are required then:
[MikroTik] ip firewall static-nat>
add dst-address 10.1.1.12/32:20-21 protocol tcp \
direction in interface Public translate yes \
to-dst-address 192.168.0.17/32
add src-address 192.168.0.17/32:20-21 protocol tcp \
direction out interface Public translate yes \
to-src-address 10.1.1.12/32
[MikroTik] ip firewall static-nat> print
Flags: X - disabled, I - invalid
0 interface=Public src-address=0.0.0.0/0:0-65535 dst-address=10.1.1.12/32:20-21
protocol=tcp to-src-address=0.0.0.0/0:0 to-dst-address=192.168.0.17/32:0
translate=yes direction=in
1 interface=Public src-address=192.168.0.17/32:20-21
dst-address=0.0.0.0/0:0-65535 protocol=tcp to-src-address=10.1.1.12/32:0
to-dst-address=0.0.0.0/0:0 translate=yes direction=out
[MikroTik] ip firewall static-nat>
Note, that the to-src-port and to-dst-port arguments have not be specified, and they have value '0', i.e., 'no translation' for ports.
Also, do not forget to exclude source address:ports 192.168.0.17:20-21 from masquerading, if it is used for local addresses:
[MikroTik] ip firewall rule forward>
add src-address 192.168.0.17/32:20-21 interface Public protocol tcp
add action masq interface Public
[MikroTik] ip firewall rule forward> print
Flags: X - disabled, I - invalid
0 protocol=tcp src-address=192.168.0.17/32:20-21
dst-address=0.0.0.0/0:0-65535 interface=Public action=accept
tcp-options=all log=no
1 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=masq
tcp-options=all log=no
[MikroTik] ip firewall rule forward>
Example of NAT and Access from the Local Network
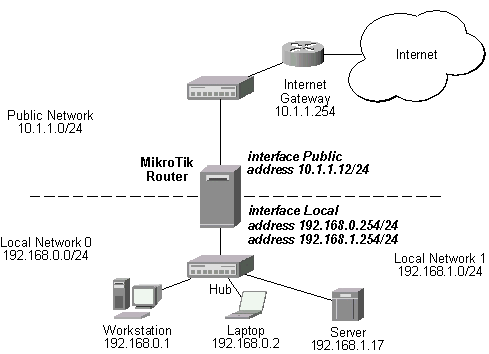
Let us reconsider the previous example of using NAT for ftp. To enable the local workstations 192.168.0.1...2 accessing the server on the local net using its global address 10.1.1.12:21, the network configuration should be changed. The requests to the server should appear as coming rather from another network than from it's own one. Then the 'backward' translation rules will be used too, since the packets would be sent back to the router.
To accomplish this:
The network diagram looks like follows:
To add another address to the router, use:
[MikroTik] ip address> add address 192.168.1.24/24 interface Local [MikroTik] ip address> print Flags: X - disabled, I - invalid, D - dynamic # ADDRESS NETWORK BROADCAST INTERFACE 0 192.168.0.254/24 192.168.0.0 192.168.0.255 Local 1 192.168.1.254/24 192.168.1.0 192.168.1.255 Local 2 10.1.1.12/24 10.1.1.0 10.1.1.255 Public [MikroTik] ip address>
Add two static NAT rules:
[MikroTik] ip firewall static-nat>
add dst-address 10.1.1.12/32:20-21 protocol tcp \
direction in translate yes to-dst-address 192.168.1.17/32
add src-address 192.168.1.17/32:20-21 protocol tcp \
direction out translate yes to-src-address 10.1.1.12/32
[MikroTik] ip firewall static-nat> print
Flags: X - disabled, I - invalid
0 interface=all src-address=0.0.0.0/0:0-65535 dst-address=10.1.1.12/32:20-21
protocol=tcp to-src-address=0.0.0.0/0:0 to-dst-address=192.168.1.17/32:0
translate=yes direction=in
1 interface=all src-address=192.168.1.17/32:20-21
dst-address=0.0.0.0/0:0-65535 protocol=tcp to-src-address=10.1.1.12/32:0
to-dst-address=0.0.0.0/0:0 translate=yes direction=out
[MikroTik] ip firewall static-nat>
Add two rules to the forward chain:
[MikroTik] ip firewall rule forward>
add src-address 192.168.1.17/32:20-21 protocol tcp interface Public
add action masq interface Public
[MikroTik] ip firewall rule forward> print
Flags: X - disabled, I - invalid
0 protocol=tcp src-address=192.168.1.17/32:20-21
dst-address=0.0.0.0/0:0-65535 interface=Public action=accept
tcp-options=all log=no
1 protocol=all src-address=0.0.0.0/0:0-65535
dst-address=0.0.0.0/0:0-65535 interface=Public action=masq
tcp-options=all log=no
[MikroTik] ip firewall rule forward>
The local workstations from Network 0 will be accessing the server on Network 1 solely through the router, and all packets will be processed against the translation rules.